Introduction
The confidentiality, integrity, and availability of information, in all its forms, are critical to the on-going functioning and good governance of Fluent Commerce.
This information security policy outlines Fluent Commerce’s approach to information security management. This policy provides the guiding principles and responsibilities necessary to safeguard the security of Fluent Commerce information systems. Supporting policies, codes of practice, procedures and guidelines provide further details.
Fluent Commerce is committed to a robust implementation of information security management. Fluent Commerce aims at ensuring the appropriate confidentiality, integrity, and availability of data. The principles defined in this policy should be applied to all physical and electronic information assets for which Fluent Commerce is responsible.
Fluent Commerce is specifically committed to preserving the confidentiality, integrity, and availability of documentation and data supplied by, generated by and held on behalf of third parties pursuant to the carrying out of work agreed by contract.
Purpose
This policy outlines how Fluent Commerce will manage and mitigate security risks to safeguard the confidentiality, integrity, and availability of information and communication technology assets and environment.
The primary purposes of this policy are to:
- Ensure the protection of all Fluent Commerce information systems (including but not limited to all computers, mobile devices, networking equipment, software, and data).
- Mitigate the risks associated with the theft, loss, misuse, damage or abuse of information systems.
- Make certain that users are aware of and comply with all current and relevant legislation.
- Provide a safe and secure information system working environment for staff, contractors, third-parties and any other authorized users.
- Ensure all users understand their own responsibilities for protecting the confidentiality and integrity of the data they handle.
- Protect Fluent Commerce from liability or damage through the misuse of Fluent's IT facilities.
- Respond to feedback and update as appropriate, initiating a cycle of continuous improvement.
Scope
This policy is applicable to, and will be communicated to, all staff, contractors and third parties who interact with information held by Fluent Commerce and the information systems used to store and process this information. This includes, but is not limited to, any systems or data attached to Fluent Commerce data or telephone networks, systems managed by Fluent Commerce, mobile devices used to connect to Fluent Commerce networks, devices used to hold Fluent Commerce data, data over which Fluent Commerce holds the intellectual property rights, data over which Fluent Commerce is the data owner or data custodian, communications sent to or from Fluent Commerce.
Definitions
Fluent Commerce Data, for the purposes of this policy, is data owned, processed or held by Fluent Commerce, whether primary or secondary, irrespective of the storage location. The phrases ‘Fluent Commerce data’, and ‘data’ are used interchangeably with the term ‘information’.
Compliance
Compliance Measurement
The Site Reliability team will verify compliance to this policy through various methods, including but not limited to, periodic walk-thru(s), monitoring, business tool reports, internal and external audits, and feedback to the respective teams
Exceptions
Any exception to the policy must be approved by the Chief Technology Officer in advance.
Non-Compliance
Any employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
All application releases must pass through the change control process. Any applications that do not adhere to this policy may be taken offline until such time that a formal assessment can be performed at the discretion of the Chief Technology Officer.
Information Security and Access
Acceptable Use
Fluent Commerce’s intentions for publishing this acceptable use policy are not to impose restrictions that are contrary to Fluent Commerce’s established culture of openness, trust, and integrity. Fluent Commerce is committed to protecting our employees, partners, and the entire organization from illegal or damaging actions by individuals, either knowingly or unknowingly.
Internet/Intranet/Extranet-related systems, including but not limited to computer equipment, software, operating systems, storage media, network accounts providing electronic mail, world wide web browsing, and FTP, are the property of Fluent Commerce. These systems are to be used for business purposes in serving the interests of Fluent Commerce, and of our clients and customers in the course of normal operations.
Effective security is a team effort involving the participation and support of every Fluent Commerce employee, contractors, and third parties who deal with information and/or information systems. It is the responsibility of every Fluent Commerce employee and partner to know these guidelines and to conduct their activities accordingly.
Monitoring and Logging
Logging from critical systems, applications and services can provide key information and potential indicators of compromise. Although logging information may not be viewed on a daily basis, it is critical to have from a forensics standpoint.
General Requirements for Monitoring and Logging
All systems that handle confidential information, accept network connections, or make access control (authentication and authorization) decisions shall record and retain audit-logging information sufficient to answer the following questions:
- What activity was performed?
- Who or what performed the activity, including where or on what system the activity was performed from (subject)?
- What the activity was performed on (object)?
- When was the activity performed?
- What tool(s) was the activity was performed with?
- What was the status (such as success vs. failure), outcome, or result of the activity?
- Detection of suspicious/malicious activity such as from an Intrusion Detection or Prevention System (IDS/IPS), anti-virus system, or anti-spyware system.
- Elements of the Log - such logs shall identify or contain at least the following elements, directly or indirectly. In this context, the term “indirectly” means unambiguously inferred.
- Type of action – examples include authorize, create, read, update, delete, and accept network connection.
- Subsystem performing the action – examples include process or transaction name, process or transaction identifier.
- Identifiers (as many as available) for the subject requesting the action – examples include username, computer name, IP address, and MAC address. Note that such identifiers should be standardized in order to facilitate log correlation.
- Identifiers (as many as available) for the object the action was performed on – examples include file names accessed, unique identifiers of records accessed in a database, query parameters used to determine records accessed in a database, computer name, IP address, and MAC address. Note that such identifiers should be standardized in order to facilitate log correlation.
- Before and after values when the action involves updating a data element, if feasible.
- Date and time the action was performed, including relevant time-zone information if not
in Coordinated Universal Time.
- Whether the action was allowed or denied by access-control mechanisms.
- Description and/or reason-codes of why the action was denied by the access-control
mechanism, if applicable.
Account Management
Fluent Commerce user accounts are centrally managed and granted by our approval process and given the minimum access level for the particular requirement.
Privileged access (e.g. admin access or access to system management software) is only granted to a limited number of staff members approved by management and is tracked and fully auditable to the individual staff member.
Usage of privileged access accounts should only be used for the duration of the task that requires the escalated level of access.
All access rights must be revoked when a user no longer needs that level or function of access.
Password Policy
Passwords are an important aspect of computer security. A poorly chosen password may result in unauthorized access and/or exploitation of Fluent Commerce's resources. All users, including contractors and vendors with access to Fluent Commerce systems, are responsible for taking the appropriate steps, as outlined below, to select and secure their passwords.
As a staff member of Fluent Commerce, you must follow the password policy.
Password Creation
- All user-level and system-level passwords must conform to the Password Construction Guidelines.
- Users must not use the same password for Fluent Commerce accounts as they do for other unrelated Fluent Commerce access (for example, personal ISP account, option trading, benefits,
and so on).
- Where possible, users must not use the same password for various Fluent Commerce access needs.
- User accounts that have system-level privileges granted through group memberships or programs such as sudo, must have a unique password from all other accounts held by that user. In particular, passwords should be different between the Sandbox and Production environments.
- All system-level passwords (for example, root, enable, application
administration accounts, and so on) must be changed on at least a quarterly basis.
All user-level passwords (for example, email, web, desktop computer, and so on) must be changed at least every six months.
Password Change
- All system-level passwords (for example, root, enable, application administration accounts, and so on) must be changed on at least a quarterly basis.
- All user-level passwords (for example, email, web, desktop computer, and so on) must be changed at least every six months.
- The admin should deactivate/change the Password for the user who no longer requires access to the app.
Password Protection
- Passwords must not be shared with anyone. All passwords are to be treated as sensitive,
Confidential Fluent Commerce information. All Passwords, keys, and certificates are only to be shared by a reference to LastPass Enterprise (for user accessible keys/passwords) and AWS Secrets Manager/CloudHSM for system account details
- Passwords must not be inserted into email messages, Alliance cases or other forms of electronic communication.
- Do not reveal a password on questionnaires or security forms.
- Do not hint at the format of a password (for example, "my family name").
- Do not share Fluent Commerce passwords with anyone, including administrative assistants, managers, co-workers while on vacation, and family members.
- Do not write passwords down and store them anywhere in your office. Do not store passwords in a file on a computer system or mobile devices (phone, tablet) without encryption.
- Any user suspecting that his/her password may have been compromised must report the
incident and change all passwords.
Application Development
Application developers must ensure that their programs contain the following security precautions:
- Applications must support authentication of individual users, not groups.
- Applications must not store passwords in clear text or in any easily reversible form.
- Applications must not transmit passwords in clear text over the network.
- Applications must provide for some sort of role management, such that one user can take
over the functions of another without having to know the other's password.
- All users, including system users, should only have access to the required APIs via the roles/permissions using the concept of least privileges (i.e., fine-grained roles).
Use of Passwords and Passphrases
Passphrases are used for public/private key authentication. A public/private key system defines a mathematical relationship between the public key that is known by all, and the private key, that is known only to the user. Without the passphrase to "unlock" the private key, the user cannot gain access.
Passphrases are not the same as passwords. A passphrase is a longer version of a password and is, therefore, more secure. A passphrase is typically composed of multiple words. Because of this, a passphrase is more secure against "dictionary attacks."
Construction Guidelines
Passwords are a critical component of information security. Passwords serve to protect user accounts; however, a poorly constructed password may result in the compromise of individual systems, data, etc. This guideline provides several best practices for creating secure passwords.
All passwords should meet or exceed the following guidelines Strong passwords have the following characteristics:
- Contain at least eight alphanumeric characters.
- Contain both upper- and lower-case letters.
- Contain at least one number (for example, 0-9).
Poor, or weak, passwords have the following characteristics:
- Contain less than eight characters.
- Can be found in a dictionary, including foreign language, or exist in a language slang,
dialect, or jargon.
* Contain personal information such as birthdates, addresses, phone numbers, or names of family members, pets, friends, and fantasy characters.
- Contain work-related information such as building names, system commands, sites, companies, hardware, or software.
- Contain number patterns such as aaabbb, qwerty, zyxwvuts, or 123321.
- Contain common words spelled backward, or preceded or followed by a number (for
example, terces, secret1 or 1secret).
* Are some version of “Welcome123” “Password123” “Changeme123”
You should never write down a password. Instead, try to create passwords that you can remember easily. One way to do this is to create a password based on a song title, affirmation, or phrase. For example, the phrase, "This May Be One Way To Remember" could become the password TmB1w2R! or another variation.
Digital Communications
- Fluent Commerce email accounts should be used primarily for Fluent Commerce business-related purposes; personal communication is permitted on a limited basis, but non- Fluent Commerce related commercial use is prohibited.
- All Fluent Commerce data contained within an email message or an attachment must be secured according to the Data Protection Standard.
- Emails should be retained only if they qualify as a Fluent Commerce business record. An email is a Fluent Commerce business record if there exists a legitimate and ongoing business reason to preserve the information contained in the email.
- The Fluent Commerce email system shall not be used for the creation or distribution of any disruptive or offensive messages, including offensive comments about race, gender, hair color, disabilities, age, sexual orientation, pornography, religious beliefs and practice, political beliefs, or national origin. Employees and partners who receive any emails with this content from any other Fluent Commerce employee and/or partner should immediately report the matter to their supervisor.
- Users are prohibited from automatically forwarding Fluent Commerce email to a third-party email system (see below point). Individual messages which are forwarded by the user must not contain Fluent Commerce confidential or above information.
- Users are prohibited from using third-party email systems and storage servers such as Yahoo, and MSN Hotmail, etc. to conduct Fluent Commerce business, to create or memorialize any binding transactions, or to store or retain email on behalf of Fluent Commerce. Such communications and transactions should be conducted through proper channels using Fluent Commerce-approved documentation.
- Using a reasonable amount of Fluent Commerce resources for personal emails is acceptable, but non-work-related email should be saved in a separate folder from work-related email.
- As an employee of Fluent Commerce, you should have no expectation of privacy in anything you store, send or receive on Fluent Commerce’s email system.
- Fluent Commerce may monitor messages without prior notice as per relevant law. Fluent Commerce is not obliged to monitor email messages.
Corporate Network Access
Wireless Access
With the mass explosion of smartphones and tablets, pervasive wireless connectivity is a given at any organization. Insecure wireless configuration can provide an easy open door for malicious threat actors.
All wireless infrastructure devices that reside at a Fluent Commerce site and connect to a Fluent Commerce network, or provide access to information classified as Fluent Commerce Confidential, or above must:
- Abide by the standards specified in the Wireless Communication Standard.
- Be installed, supported, and maintained by an approved support team.
- Use Fluent Commerce approved authentication protocols and infrastructure.
- Use Fluent Commerce approved encryption protocols.
- Maintain a hardware address (MAC address) that can be registered and tracked.
- Not interfere with wireless access deployments maintained by other support organizations.
Remote Access
Remote access to our corporate network is essential in maintaining our team’s productivity, but in many cases, this remote access originates from networks that may already be compromised or are at a significantly lower security posture than our corporate network. While these remote networks are beyond the control of Fluent Commerce policy, we must mitigate these external risks to the best of our ability.
It is the responsibility of Fluent Commerce employees, contractors, vendors and agents with remote access privileges to Fluent Commerce's corporate network to ensure that their remote access connection is given the same consideration as an on-site connection to Fluent Commerce.
General access to the Internet through the Fluent Commerce network is limited to Fluent Commerce employees, contractors, vendors, and agents (hereafter referred to as “Authorized Users”). When accessing the Fluent Commerce network from a personal computer, Authorized Users are responsible for preventing access to any Fluent Commerce computer resources or data by non-Authorized Users. Performance of illegal activities through the Fluent Commerce network by any user (Authorized or otherwise) is prohibited. The Authorized user bears responsibility for and consequences of any misuse of the Authorized User’s access. For further information and definitions, see the Acceptable Use Policy. All remote access is tracked and subject to routine audits.
Authorized Users will not use Fluent Commerce networks to access the Internet for outside business interests.
For additional information regarding Fluent Commerce's remote access connection options, including how to obtain a remote access login, free anti-virus software, troubleshooting, etc., go to the Remote Access Services website.
- Secure remote access must be controlled with encryption (i.e., Virtual Private Networks (VPNs)) and strong pass-phrases.
- Authorized Users shall protect their login and password via the provided password/key manager and use 2-factor authentication via Google Authenticator.
- While using a Fluent Commerce-owned computer to remotely connect to Fluent Commerce's corporate network, Authorized users must ensure the remote host is not connected to any other network at the same time, with the exception of personal networks that are under their complete control or under the complete control of an Authorized user or third party.
- All hosts that are connected to Fluent Commerce internal networks via remote access technologies must use the most up-to-date anti-virus software, this includes personal computers. Third party connections must comply with requirements as stated in the Third-Party Agreement.
- Personal equipment used to connect to Fluent Commerce's networks must meet the requirements of Fluent Commerce-owned equipment for remote access as stated in the Hardware and Software Configuration Standards for Remote Access to Fluent Commerce Networks.
Platform Service Access
Unsecured and vulnerable servers continue to be a major entry point for malicious threat actors. Consistent server installation policies, ownership, and configuration management are all about doing the basics well.
All internal servers deployed at Fluent Commerce must be owned by an operational group that is responsible for system administration. Approved server configuration guides must be established and maintained by each operational group, based on business needs. Operational groups should monitor configuration compliance and implement an exception policy tailored to their environment. Each operational group must establish a process for changing the configuration guides, which includes reviewing and gaining approval from an identified source.
Servers must be registered within the corporate enterprise management system. At a minimum, the following information is required to positively identify the point of contact:
- Server contact(s) and location, and a backup contact. Hardware and Operating System/Version.
- Main functions and applications, if applicable. Information in the corporate enterprise management system must be kept up-to-date.
- Configuration changes for production servers must follow the appropriate change management procedures.
- For security, compliance, and maintenance purposes, authorized personnel may monitor and audit equipment, systems, processes, and network traffic.
Configuration Requirements
- Operating System configuration should be in accordance with approved guidelines.
- Services and applications that will not be used must be disabled where practical.
- Access to services should be logged and/or protected through access-control methods such as a web application firewall, if possible.
- The most recent security patches must be installed on the system as soon as practical, the only exception being when the immediate application would interfere with business
requirements.
- Trust relationships between systems are a security risk, and their use should be avoided.
- Do not use a trust relationship when some other method of communication is sufficient.
- Always use standard security principles of least required access to perform a function.
- Do not use root when a non-privileged account will do.
- If a methodology for secure channel connection is available (i.e., technically feasible),
- privileged access must be performed over secure channels, (e.g., encrypted network connections using SSH or IPSec).
- Servers should be physically located in an access-controlled environment.
- Servers are specifically prohibited from operating from uncontrolled cubicle areas.
Monitoring
All security-related events on critical or sensitive systems must be logged and audit trails saved as follows:
- All security related logs must be kept online for a minimum of 1 week.
- Daily incremental tape backups must be retained for at least 1 month.
- Weekly full tape backups of logs must be retained for at least 1 month.
- Monthly full backups must be retained for a minimum of 2 years.
Security-related events will be reported to the Security team, who will review logs and report incidents to IT management. Corrective measures will be prescribed as needed. Security-related events include, but are not limited to the following:
- Port-scan attacks.
- Evidence of unauthorized access to privileged accounts.
- Anomalous occurrences that are not related to specific applications on the host.
Platform Data Security
Encryption
Encryption Key Management, if not done properly, can lead to compromise and disclosure of private keys used to secure sensitive data. While users may understand that it’s important to encrypt certain documents and electronic communications, they may not be familiar with minimum standards for protecting encryption keys.
All encryption keys covered by this policy must be protected to prevent their unauthorized disclosure and subsequent fraudulent use.
- Keys used for secret key encryption, also called symmetric cryptography, must be protected as they are distributed to all parties that will use them. During distribution, the symmetric encryption keys must be encrypted using a stronger algorithm with a key of the longest key length for that algorithm authorized in Fluent Commerce’s Acceptable Encryption Policy. If the keys are for the strongest algorithm, then the key must be split, each portion of the key encrypted with a different key that is the longest key length authorized and each encrypted portion is transmitted using different transmission mechanisms. The goal is to provide more stringent protection to the key than the data that is encrypted with that encryption key.
- Symmetric encryption keys, when at rest, must be protected with security measures at least as stringent as the measures used for distribution of that key.
- Public key cryptography, or asymmetric cryptography, uses public-private key pairs. The public key is passed to the certificate authority to be included in the digital certificate issued to the end user. The digital certificate is available to everyone once it is issued. The private key should only be available to the end user to whom the corresponding digital certificate is issued.
- Public Key Encryption Keys types of keys may be generated in software on the end user’s computer and can be stored as files on the hard drive or on a hardware token. If the public-private key pair is generated on a smartcard, the requirements for protecting the private keys are the same as those for private keys associated with Fluent Commerce Public Key Infrastructure (PKI). If the keys are generated in software, the end user is required to create at least one backup of these keys and store any backup copies securely. The user is also required to create an escrow copy of any private keys used for encrypting data and delivering the escrow copy to the local Information Security representative for secure storage.
- Commercial or Outside Organization Public Key Infrastructure (PKI) Keys
in working with business partners, the relationship may require the end users to use public-private key pairs that are generated in software on the end user’s computer. In these cases, the public-private key pairs are stored in files on the hard drive of the end user. The private keys are only protected by the strength of the password or passphrase chosen by the end user. For example, when an end user requests a digital certificate from a commercial PKI, such as VeriSign or Thawte, the end user’s web browser will generate the key pair and submit the public key as part of the certificate request to the CA. The private key remains in the browser’s certificate store where the only protection is the password on the browser’s certificate store. A web browser storing private keys will be configured to require the user to enter the certificate store password anytime a private key is accessed.
- PGP Key Pairs: If the business partner requires the use of PGP, the public-private key pairs can be stored in the user’s key ring files on the computer hard drive or on a hardware token, for example, a USB drive or a smart card. Since the protection of the private keys is the passphrase on the secret keying, it is preferable that the public-private keys are stored on a hardware token. PGP will be configured to require entering the passphrase for every use of the private keys in the secret key ring.
- Hardware Token Storage: Hardware tokens storing encryption keys will be treated as sensitive company equipment, as described in Fluent Commerce’s Physical Security policy when outside company offices. In addition, all hardware tokens, smartcards, USB tokens, etc., will not be stored or left connected to an end user’s computer when not in use. For end users traveling with hardware tokens, they will not be stored or carried in the same container or bag as any computer.
- Personal Identification Numbers (PINs), Passwords and Passphrases
, all PINs, passwords or passphrases used to protect encryption keys must meet complexity and length requirements described in Fluent Commerce’s Password Policy.
- Loss and Theft: The loss, theft, or potential unauthorized disclosure of any encryption key covered by this policy must be reported immediately to The Tech Team. Tech personnel will direct the end user in any actions that will be required regarding revocation of certificates or public-private key pairs.
Database Access
Database authentication credentials are a necessary part of authorizing an application to connect to internal databases. However, incorrect use, storage, and transmission of such credentials can lead to the compromising of sensitive assets and can also be a springboard to wider compromise within the organization.
In order to maintain the security of Fluent Commerce's internal databases, access by software programs must be granted only after authentication with credentials. The credentials used for this authentication must not reside in the main, executing body of the program's source code in clear text. Database credentials must not be stored in a location that can be accessed through a web server.
- Database usernames and passwords may be stored in a file separate from the executing body of the program's code. This file must not be world readable or writeable.
- Database credentials may reside on the database server. In this case, a hash function number identifying the credentials may be stored in the executing body of the program's code.
- Database credentials may be stored as part of an authentication server (i.e., an entitlement directory), such as an LDAP server used for user authentication. Database authentication may occur on behalf of a program as part of the user authentication process at the authentication server. In this case, there is no need for programmatic use of database credentials.
- Database credentials may not reside in the documents tree of a web server.
- Pass through authentication must not allow access to
the database based solely upon a remote user's authentication on the remote host.
- Passwords or passphrases used to access a database must adhere to the Password Policy. Retrieval of Database usernames and passwords must be conducted through secure channels, ensuring that the credentials are encrypted during transmission and storage.
Processing Personal Data
Any and all personal data collected by Fluent Commerce is collected in order to ensure that Fluent Commerce can facilitate efficient transactions with third parties including, but not limited to, its customers, partners, associates, and affiliates. Personal data is collected to efficiently manage Fluent Commerce employees, contractors, agents, and consultants. Personal data may also be used by Fluent Commerce in meeting any and all relevant obligations imposed by law.
Personal data may be disclosed within Fluent Commerce. Personal data may be passed from one department to another in accordance with the data protection principles and this Policy. Under no circumstances will personal data be passed to any department or any individual within Fluent Commerce that does not require access to that personal data with respect to the purpose(s) for which it was collected and is being processed.
Fluent Commerce shall ensure the following:
- All personal data collected and processed for and on behalf of Fluent Commerce by any party is collected and processed fairly and lawfully.
- Data subjects are made fully aware of the reasons for the collection of personal data and are given details of the purpose for which the data will be used.
- Personal data is only collected to the extent that is necessary to fulfill the stated purpose(s).
- All personal data is accurate at the time of collection and kept accurate and up-to-date while it is being held and/or processed.
- No personal data is held for any longer than necessary in light of the stated purpose(s).
- All personal data is held in a safe and secure manner, taking all appropriate technical and organizational measures to protect the data. All personal data is transferred using secure means, electronically or otherwise.
- No personal data is transferred outside of Australia without first ensuring that appropriate safeguards are in place in the destination country or territory.
- All data subjects can exercise their rights set out above in Section 3 and more fully in the Act.
- Fluent Commerce will ensure that all of its employees, contractors, agents, consultants, partners or other parties working on behalf of the company comply with the following when processing and/or transmitting personal data:
- All emails containing personal data must be encrypted.
- Personal data may be transmitted over secure networks only – transmission over unsecured networks is not permitted in any circumstances.
- Personal data may not be transmitted over a wireless network if there is a wired alternative that is practicable.
- Personal data contained in the body of an email, whether sent or received, should be copied from the body of that email and stored securely. The email itself should be deleted. All temporary files associated therewith should also be deleted.
- Where personal data is to be sent by facsimile transmission the recipient should be informed in advance of the transmission and should be waiting by the fax machine to receive the data.
- Where Personal data is to be transferred in hardcopy form it should be passed directly to the recipient. Using an intermediary is not permitted.
- All hard copies of personal data should be stored securely in a locked box, drawer, cabinet or similar.
- All electronic copies of personal data should be stored securely using passwords and suitable data encryption, where possible on a drive or server which cannot be accessed via the internet.
- All passwords used to protect personal data should be changed regularly and should not use words or phrases which can be easily guessed or otherwise compromised.
Technology Equipment
Technology equipment often contains parts which cannot simply be thrown away. Proper disposal of equipment is both environmentally responsible and required by law. In addition, hard drives, USB drives, and other storage media contain various kinds of Fluent Commerce data, some of which is considered sensitive.
Workstation Security
The purpose of this policy is to provide guidance for workstation security for Fluent Commerce workstations in order to ensure the security of information on the workstation and information the workstation may have access to.
Appropriate measures must be taken when using workstations to ensure the confidentiality, integrity, and availability of sensitive information, including protected health information (PHI) and ensuring access to sensitive information is restricted to authorized users.
Fluent Commerce will implement physical and technical safeguards for all workstations that access electronically protected health information to restrict access to authorized users.
Appropriate measures include the following:
- Restricting physical access to workstations to only authorized personnel.
- Securing workstations (screen lock or log out) prior to leaving the area to prevent unauthorized access.
- Workstations must be configured with an auto lock on 2 minutes of idle time. Enabling a password-protected screen saver with a short timeout period to ensure that workstations that were left unsecured will be protected. The password must comply with Fluent Commerce Password Policy.
- Ensuring workstations are used for authorized business purposes only.
- Never installing unauthorized software on workstations.
- Storing all sensitive information
- Keeping food and drink away from workstations in order to avoid accidental spills.
- Securing laptops that contain sensitive information by using cable locks or locking laptops up in drawers or cabinets.
- Complying with the Portable Workstation Encryption Policy
- Complying with the Baseline Workstation Configuration Standard
- Installing privacy screen filters or using other physical barriers to alleviate exposing data.
- Ensuring workstations are left on but logged off in order to facilitate after-hours updates.
- Exit running applications and close open documents
- Ensuring that all workstations use a surge protector (not just a power strip)
- If wireless network access is used, ensure access is secure by following the Wireless Communication policy.
Software installation
Allowing employees to install software on company computing devices opens the organization up to unnecessary exposure. Conflicting file versions which can prevent programs from running, the introduction of malware from infected installation software, unlicensed software which could be discovered during an audit, and programs which can be used to hack the organization’s network are examples of the problems that can be introduced when employees install software on company equipment.
- Employees may not install software on Fluent Commerce’s computing devices operated within the Fluent Commerce network.
- Software requests must first be approved by the requester’s manager and then be made to the Tech team in writing or via email.
- Software must be selected from an approved software list, maintained by the Information Technology department unless no selection on the list meets the requester’s need.
- The Tech team will obtain and track the licenses, test new software for conflict and compatibility, and perform the installation.
Disposal
Data Erasure
In order to protect our constituent’s data, all storage mediums must be properly erased before being disposed of. However, simply deleting or even formatting data is not considered sufficient. When deleting files or formatting a device, data is marked for deletion but is still accessible until being overwritten by a new file.
Equipment Disposal
When technology assets have reached the end of their useful life, they should be sent to the regional office for proper disposal including:
- All storage mediums
- All electronic drives
- Computer Equipment such as desktop, laptop, tablet or netbook computers, printers, copiers, monitors, servers, handheld devices, telephones, cell phones, disc drives or any storage device, network switches, routers, wireless access points, batteries, backup tapes, etc.
Vulnerability Detection and Management
The Fluent Commerce threat and vulnerability management process is a cyclical practice of identifying, assessing, classifying, remediating, and mitigating security weaknesses.
Vulnerability Assessment
All devices connected to both public and private network segments are subject to vulnerability scans and audits. The vulnerability scans are scheduled before major changes of the platform and on a scheduled basis. Vulnerability scans are done at the Network, host and application level. Any findings are reported to management for a risk assessment.
Risk Assessment
The risk assessment is the basis of identification and prioritization of information security risks. The Fluent Commerce risk assessment includes the following key steps:
- Identification and prioritization of threats and vulnerabilities
- Identifying which threats can exploit a vulnerability
- Identification of the impact to the confidentiality, integrity, and availability of sensitive data if a threat exploits a specific vulnerability; and Identification and definition of measures and/or controls used to protect the confidentiality, integrity, and availability of Information Resources
Each vulnerability is assigned a priority with the following criteria:
- SEV1 Critical Risk: The risk of imminent compromise or loss of Sensitive Data from either external or internal sources or where Sensitive Data has already been exposed.
- SEV2 High Risk: The risk of imminent compromise or loss of Sensitive Data from either external or internal sources.
- SEV3 Medium Risk: The risk of compromise or loss of Sensitive Data is possible from either external or internal sources, although less likely from external sources.
- SEV4 Low Risk: The risk of compromise or loss of sensitive Data is possible, but not probable or an Information Resource might be used to obtain access to Sensitive Data on a different Information Resource.
Vulnerability Management
All current vulnerabilities are reported and tracked with their associated risk in our Vulnerability and Risk management project in JIRA. Any vulnerability with unacceptable risk has a tracked project item to deliver corrective actions or mitigation. Vulnerabilities that are determined to be false positives are also recorded once approved.
Incident Management
The incident management process operates in accordance with the Fluent Commerce Service Level Agreement as determined by the Terms and Conditions.
The diagram below provides an outline of the security incident process. Please refer to the Service Level Agreement for specific response and resolution times.
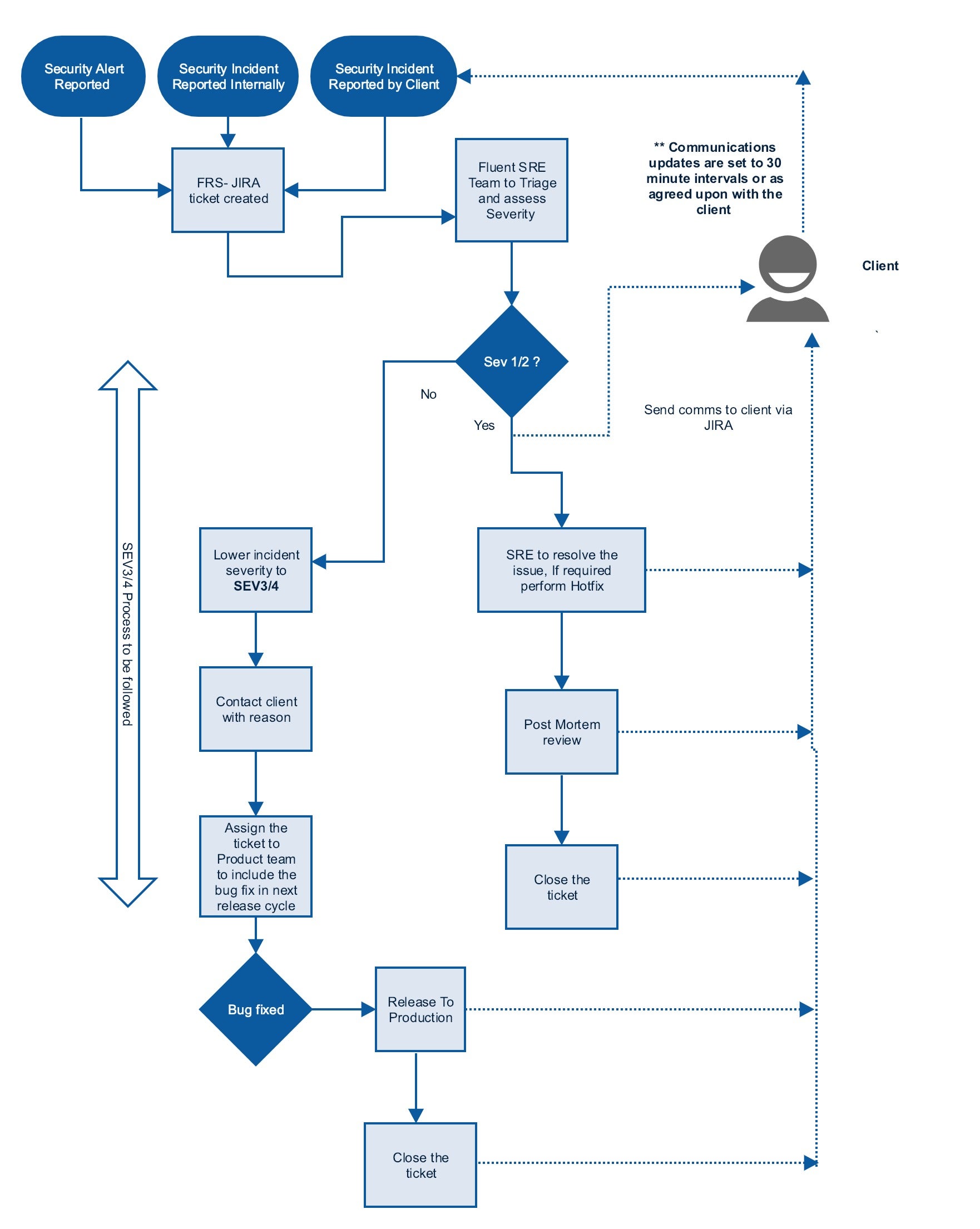
Secure Software Development
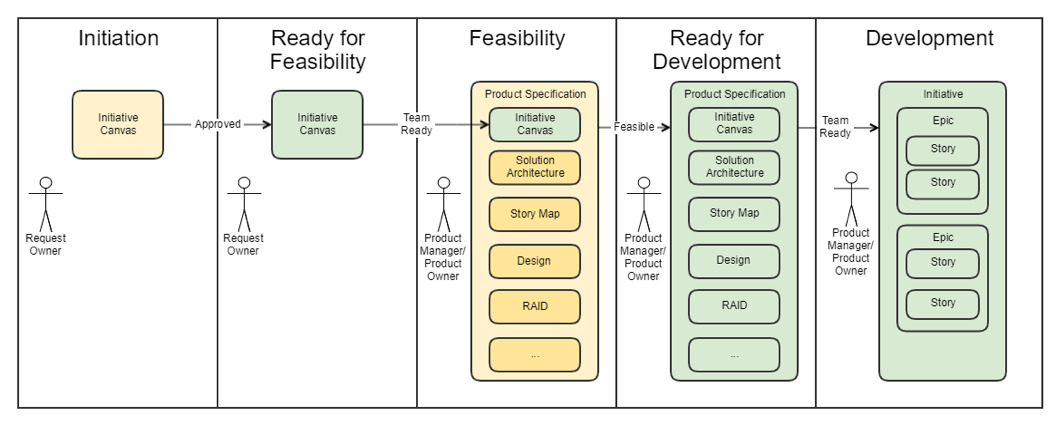
Development Lifecycle
The diagrams below show stages of the Fluent Commerce Software Development Framework.
High Level Initiative Flow Diagram
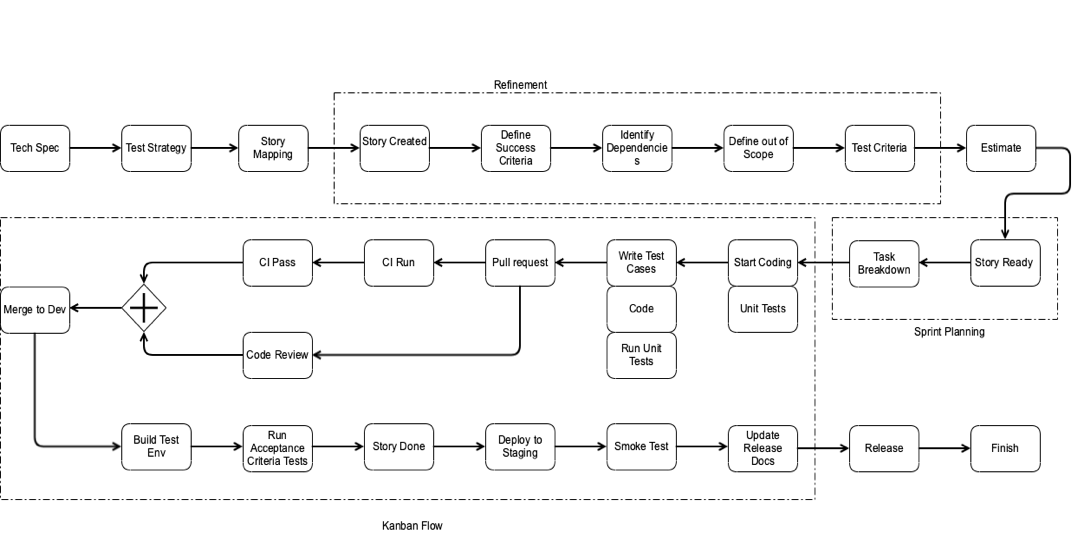
Detail Flow Diagram
Development lifecycle stages:
- Initiative phase: In this phase, we evaluate the business need and value of a software change.
- Feasibility phase
- Requirements definition: In this phase, we ensure the best practices for security are integrated into the product. These practices are coming from industry standards and are based on responses for problems that have occurred in the past. Requirements exist to define the functional security requirements implemented in the product and include all the activities of the SDL. They are used as an enforcement point to ensure that all aspects are properly considered. Requirements are expressed as user stories. These stories contain the same information as do the requirements, but security functionality is written from the user's perspective
- Requirements review: In this phase, we assess risks and security implications and the impact on the platform. During this process, necessary changes could be applied to the requirement specification.
- Design phase: This phase is about creating an architecture and then searching for security gaps and using thread modeling. Threat modeling is the process of thinking through how a feature or system will be attacked, and then mitigating those future attacks in the design before writing the code. The design phase is about identifying security issues early in the process.
- **Development **
- Code Development: This phase is about writing secure code. The process involves a mixture of standards and automated tools.
- Quality assurance phase: We apply security functional test plans, vulnerability scanning, and penetration testing. Vulnerability scanning uses industry-standard tools (SonarCube, Nexus, Nessus, Tenable Cloud) to determine if any system-level vulnerabilities exist with the application or product. Penetration testing involves testers attempting to work around the security protections in a given application and exploit them. Pen testing stretches the product and exposes it to testing scenarios that automated tools cannot replicate. Pen testing is resource-intensive, so it's usually not performed for every release. During this process, necessary changes could be applied to the code, design or requirements when necessary.
- Release phase: Release occurs when all the security activities are confirmed against the final build and the software is made available to clients.
Secure Development Policy
- The scope into which you may store credentials must be physically separated from the other areas of your code, e.g., the credentials must be in a separate source file. The file that contains the credentials must contain no other code but the credentials (i.e., the username and password) and any functions, routines, or methods that will be used to access the credentials.
- For languages that execute from source code, the credentials' source file must not reside in the same browsable or executable file directory tree in which the executing body of code resides.
- Every program or every collection of programs implementing a single business function must have unique database credentials. Sharing of credentials between programs is not allowed.
- Database passwords used by programs are system-level passwords as defined by the Password Policy.
- Developer groups must have a process in place to ensure that database passwords are controlled and changed in accordance with the Password Policy. This process must include a method for restricting knowledge of database passwords to a need-to-know basis.
- No passwords, keys or other credentials for production access are to be stored in source code control systems. There are automated exclusion measures to exclude these from being built into application binaries
- Untrusted content is any content provided by any user and submitted to Fluent Commerce servers or being passed into Fluent Commerce code. Use of untrusted content includes saving or querying data from any datastore. All untrusted content must be processed with our agreed security encoding libraries. The libraries escape, remove or encode any untrusted content prior to use. The relevant encoding type for the content is to be used including XML, HTML, JavaScript, CSS, and SQL when using the security encoding libraries
- Any production configured external endpoints must be configured to use SSL or TLS as defined by our encryption policy. This includes the database, messaging and web service endpoints.
- All third-party software components or libraries included application builds must come from Fluent Commerce application repositories or agreed 3rd party application repositories. All components and libraries are to be clearly and uniquely identified including package names and exact versions to allow for easy review, audit, and update.
- Application code can only access files that contain configuration or logs. Any other data or state is only stored in an agreed and secured datastore. No other filesystem access is permitted.
- Any security event is to be logged and an event raised in our security and application event tracking systems. This includes failed login attempts, invalid untrusted content or repeated unauthorized requests.
Our implementation tools include code coverage, performance testing, and a security scan.
Business Continuity and Disaster Recovery
High Availability
All Fluent Commerce business and platform software including data are stored on highly available cloud-based services and data centers.
In the case of the Fluent Commerce platform, all software services and data are stored on Amazon Web Services regional data centers each with at least three availability zones.
In the event of a failure of any service or node, load balancer automatically redirects traffic to healthy nodes. In the event of additional load, additional nodes and services are added across availability zones.
Backups and Recovery
The backup and maintenance of Fluent Commerce data are critical to the viability and operations of Fluent Commerce. It is essential that certain basic standard practices be followed to ensure that data files are backed up on a regular basis.
Fluent Commerce will ensure the following:
- Data is backed up with the following schedule
- Hourly point in time snapshots to encrypted online storage
- Daily full backups to an encrypted online storage
- Regular archived backup for long-term storage
- Backups are always stored in our cloud-based data center.
- Routinely scheduled test restore are conducted for both full and partial restore scenarios and are verified to be correct.
- All backup and archive data are stored on at least two regional data centers.
In the case of either a test restore or a full production restore, Fluent Commerce will re-execute its customer data lifecycle management.
Business Continuity
Information Systems
Fluent Commerce business teams must use the following information systems for all business activity:
- Google Apps for email and document management.
- Google Drive for file storage.
- Atlassian Confluence Wiki for knowledge management.
Business Continuity
In the event of any major disaster or unavailability of office locations, all staff can access information systems remotely either from an alternative office or from home.
Platform Disaster Recovery
All platform services and data are served from a primary regional cloud-based data center. Each regional data center has three availability zones.
All services and data are served and stored across all availability zones. All data is backed up and archived to a sister regional cloud-based data center.
In the event of an availability zone failure, the Fluent Commerce platform automatically redirects requests to alternate availability zones with no impact to services.
In the event of a regional data center failure Fluent Commerce can restore an entire service within 24 hours.
Training, Awareness, and Reviews
Information Security Training Policies
With the aim to ensure the team understands the best information security practices, we ensure that staff read the Fluent Commerce Information Security Policy and associated questionnaires and documentation to demonstrate learning and understanding as part of employee onboarding and after any changes/improvements are made. Below are several screenshots of our Staff policy and training solution.
Software Development Security Training
Fluent Commerce ensures that software engineers are properly trained in secure coding techniques through the following mechanisms.
As part of the onboarding process, Fluent's software engineers have a security induction with a senior security engineer to talk about the most critical web application security risks. To ensure training is kept up to date, Fluent uses the latest version of the “OWASP Top 10” document as a guide for this induction.
In addition, Fluent software developers have another security induction meeting to talk exclusively about security for AWS. Fluent uses the AWS Best Practices Whitepaper as a reference for this induction.
As an ongoing process, the Engineering Team has a fortnightly “Security Guild Meeting”. In this meeting, senior security team members perform training sessions to increase security awareness across the organization.
Every time a change is committed to the source code, a senior developer from the “Security review group” has to approve the commit. This process is also used as a coaching opportunity to share security knowledge across the team.
Security Review of Application Design and Implementation
New features and changes undergo a specification process that includes Information security and data privacy considerations and reviews from security stakeholders.
All product changes are merged into our “master” version control branch before going into production. Changes to this branch are reviewed and approved by members of the “Security Review” Group. Only after this review, can code follow our build and deployment process which involves automated security checks (code analysis and vulnerability scanning).
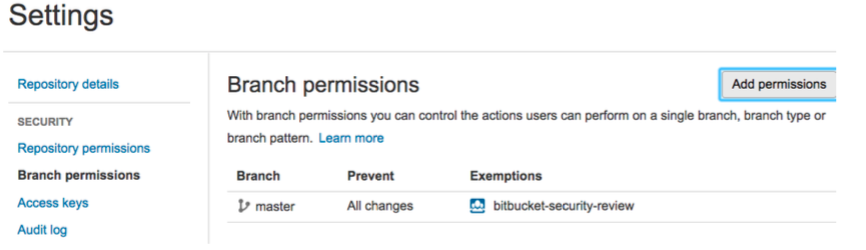
Security Mechanisms
User and Credential Management
The following security policies are in place to ensure that users have the correct level of access.
Accounts for internal systems are managed using a centralized LDAP directory located in a management network managed by SRE. All individual and shared passwords are stored in LastPass, this includes; access to external systems, internal build systems, ticketing systems, documentation tools, LastPass is also protected with two-factor authentication.
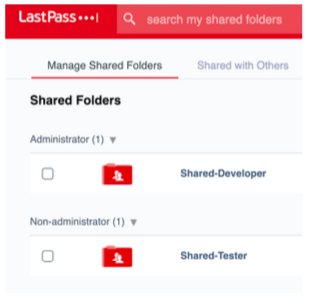
System Accounts or Credentials
IAM and Secrets Manager
We generate passwords and keys when an environment is created and store them in AWS Secrets Manager automatically. These passwords are rotated every 30 days automatically. Employees do not have access to the actual passwords.
Environment Access Restriction
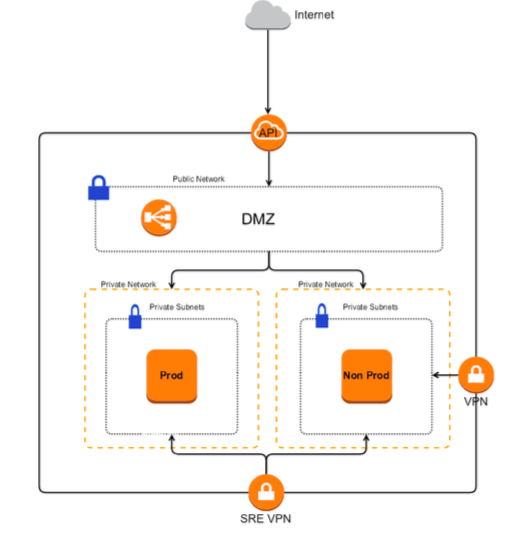
- SRE VPN: Fluent Commerce employees are able to access internal services such as ticketing and documentation systems through a VPN. Only escalated users (SRE engineers and Senior staff) have access to the Fluent Cloud platforms through the VPN. Users are required to enter credentials and 2FA when accessing the VPN.
- Office VPN: As above; Employees have access to internal ticketing and documentation tools through the office VPN. SRE engineers and senior engineers have access to the Fluent Cloud platforms using the SRE VPN
- Network: All Network related infrastructure mentioned below is generated using templates that are audited on a regular basis. The deployment process ensures that this infrastructure is tractable.
- Subnets: Each Fluent cloud is created using a combination of 3 private subnets and 3 public availability zones. This ensures redundancy and security. Only the load balancers and WAF(Web application firewall) are deployed to the public subnets to create a DMZ. All servers and data reside within Private VPC and private subnets
- ACLs: ACLs are used to restrict access to the Fluent cloud network via both egress and ingress rules.
Environment Access Security Diagram
Encryption Protocols and Ciphers
Application Authentication
- SSL / TLS: Fluent uses AWS ACM to provide SSL/TLS certificates which are renewed on a regular basis (and requests a public certificate from Amazon). By default, public certificates are trusted by browsers and operating systems. The keys for certificates are managed via AWS PKI and the Cloud-based HSM
- Access to Audit Trails and Logs: The majority of audit events are provided via our Event API. These audit events are stored and processed on isolated and dedicated database storage. Details on how to search and retrieve these events are covered in our platform documentation, Lingo.
Fluent is a multi-tenanted platform, and as such, several infrastructure level SIEM events are not available to clients and are reviewed, analyzed and audited by Fluent's security and SRE team members.
Security Policy
Equipment and Media Removal
All Employee laptops are password protected as per our password policy. A Full Disk Encryption policy is enforced. A VPN is required to access any data center resources.
Only SRE Engineers have access to client data and this data is only accessible through the VPN. No client data is stored locally. This is enforced by our policies and the above credential management processes to make sure that only authorized infrastructure has access to the keys needed to access the data. Employees must immediately notify management in the event that a device containing in scope data is lost (e.g. mobiles, laptops, etc).
When staff equipment is to be disposed of, a secure wipe is performed and then the equipment is stored at head office, and then logged and securely destroyed in accordance with ISO 27002 (A.8.3.2 – Disposal of media, A.11.2.7 – Secure disposal or reuse of equipment).
Data Center Policies
Physical data center access is only given to approved employees. All employees who need data center access must first apply for access and provide a valid business justification. These requests are granted based on the principle of least privilege, where requests must specify to which layer of the data center the individual needs access and are time-bound. Requests are reviewed and approved by authorized personnel, and access is revoked after the requested time expires. Once granted admittance, individuals are restricted to areas specified in their permissions.
Policy and Process Review and Improvement
After an incident is solved, Fluent Commerce proceeds with the following steps:
- Conduct a post-incident review meeting to analyze the cause of the incident.
- Remedy any identified security flaws – changes should be reflected in data security policies and training documents.
- Any long-term corrective actions are planned and rolled out. This can include technology, process, procedure, training or human resource changes.
- Rolling out training on any changes to relevant personnel to ensure that everyone is up to speed on the latest practices.
Every quarter, audits are conducted and involve the following:
- Reviewing that continuously automated policy tests are running successfully (Password controls, Secure development scans, Automated Vulnerability scans) and that automated security test cases are running and results are being correctly recorded and logged.
- Known security risks and security policy exceptions are reviewed with stakeholders to ensure data is correct.
- Audit of current staff role and group memberships to ensure correct access levels. Review ruleset, policies, and scans of network ACL, WAF, Vulnerability and secure development code analysis scans are valid and up to date.
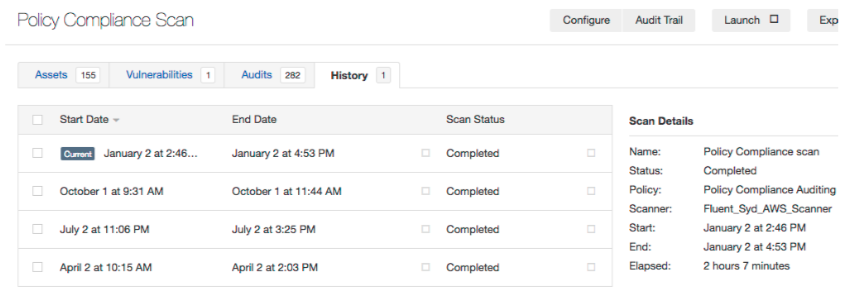
- Run Policy scan across production and non-production platform. This checks and tests for a variety of security policy items (e.g. Password, encryption, login, software update standards, etc). The screenshot below displays the compliance policy scan history.
Exception Process
Security Compliance must be viewed as a requirement for everyone. In a small number of circumstances, it may not be possible to comply, and an exception must be requested.
All Exceptions are reviewed and approved by the CTO or CSO. Exceptions are then logged and reviewed monthly.
An exception MAY be granted for non- compliance in the case of:
- Implementation of a solution with equivalent/superior protection. The impending retirement of a legacy system.
- Inability to implement the standard due to some limitation.
- Exceptions are granted for a specific period of time, not to exceed one month and are reviewed on a case-by-case basis and their approval is not automatic.







